GREENCYCLE 4 Set Wireless Bluetooth Home Store Security Burglar Alert, Vibration and Magnet Alarm Sensors with Light Flash for Windows and Doors, Intelligent Magnetic Alarm, 4 Working Mode,App Control - Walmart.com

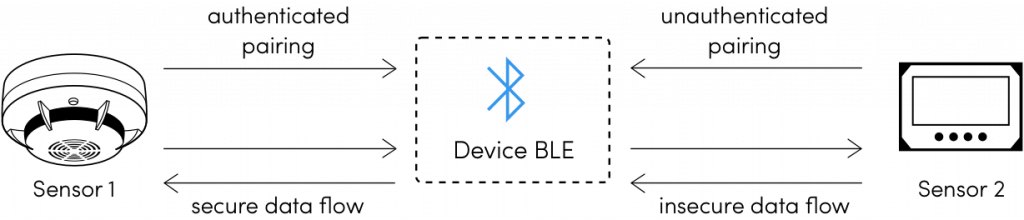
PDF) Bluetooth MITM Vulnerabilities: A Literature Review, Novel Attack Scenarios, Novel Countermeasures, and Lessons Learned

GREENCYCLE Wireless Bluetooth Home Store Security Burglar Alert, Vibration and Magnet Alarm Sensors with Red Light Flash for Windows and Doors, Intelligent Magnetic Alarm, 4 Working Mode,App Control - Walmart.com
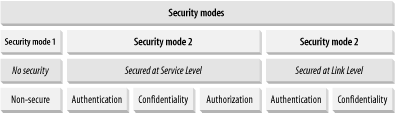
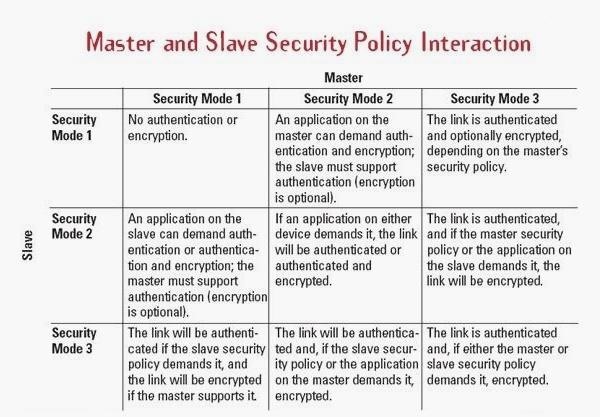
6.7 Bluetooth Security :: Chapter 6. Bluetooth :: Windows XP unwired :: Microsoft Products :: eTutorials.org
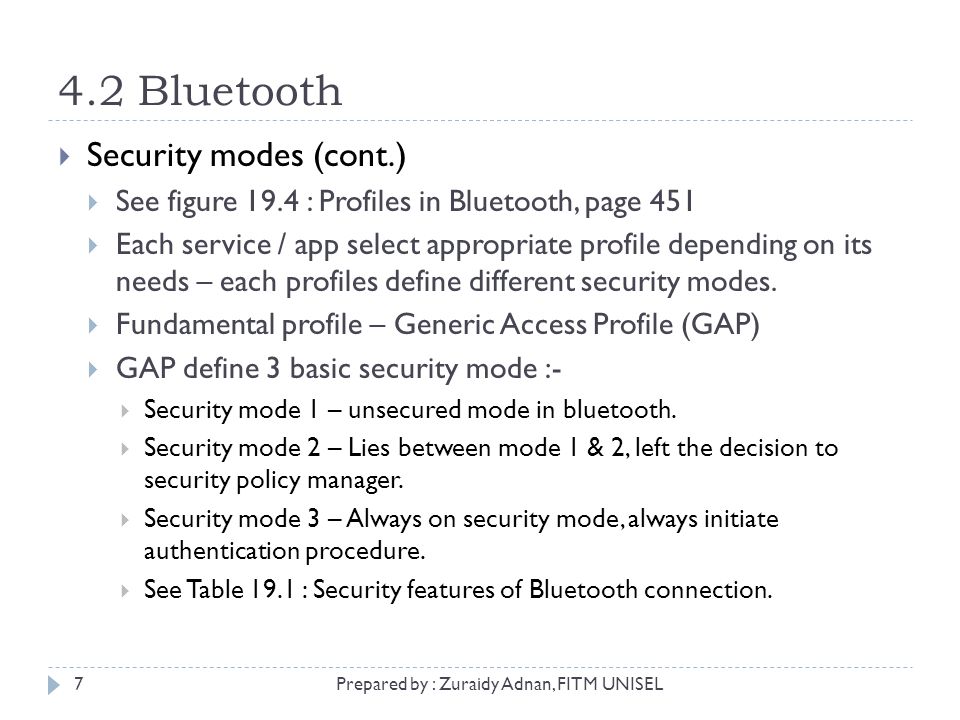
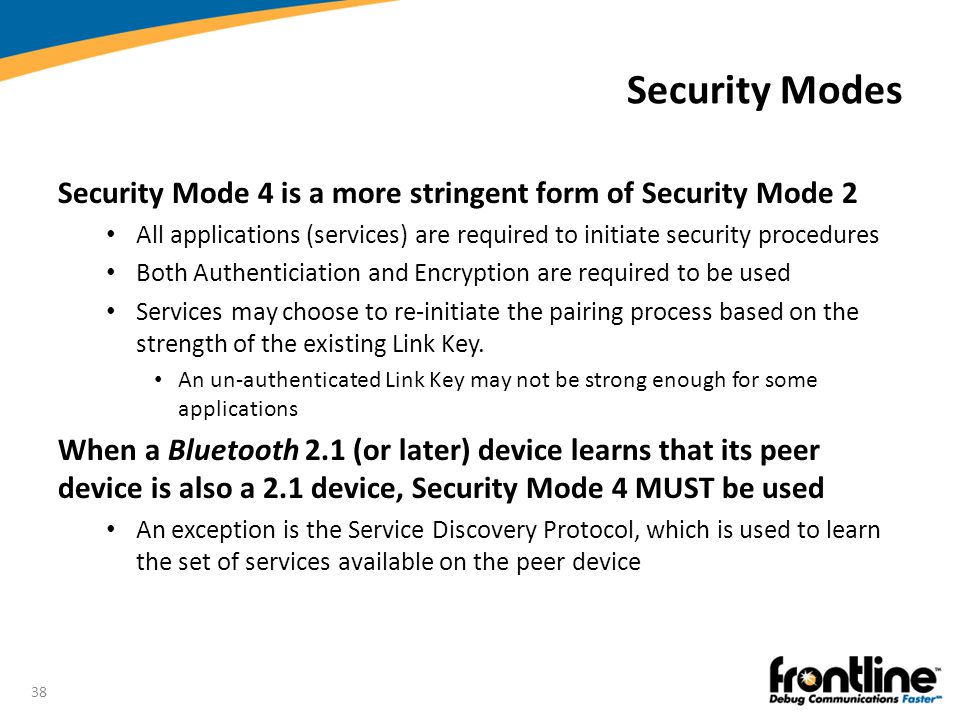
IWD2243 Wireless & Mobile Security Chapter 4 : Security in Wireless Ad Hoc Network Prepared by : Zuraidy Adnan, FITM UNISEL1. - ppt download

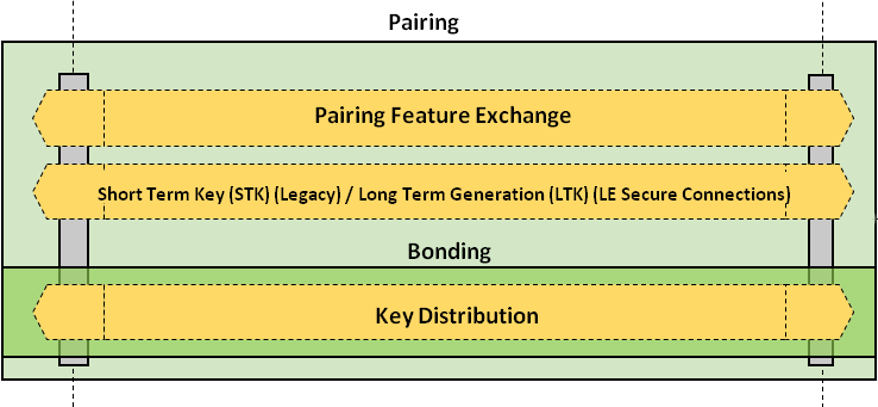
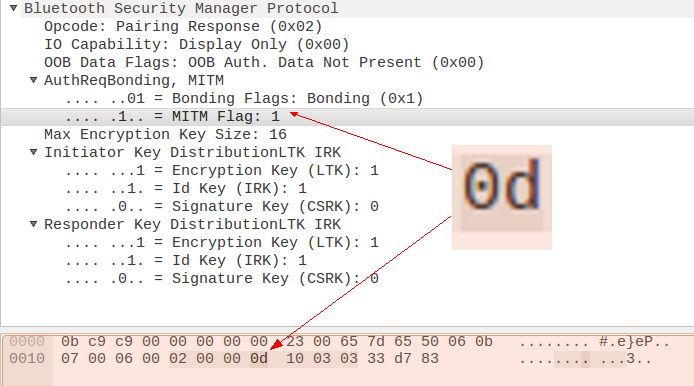
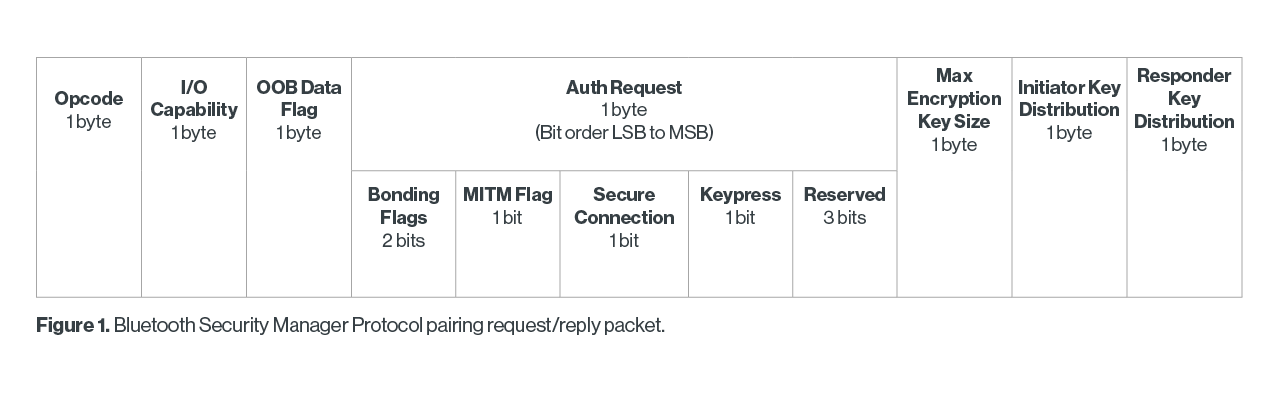
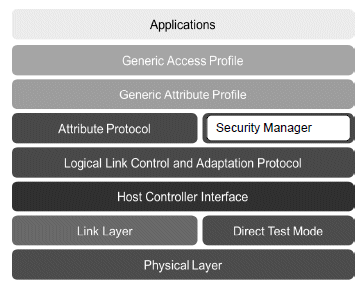
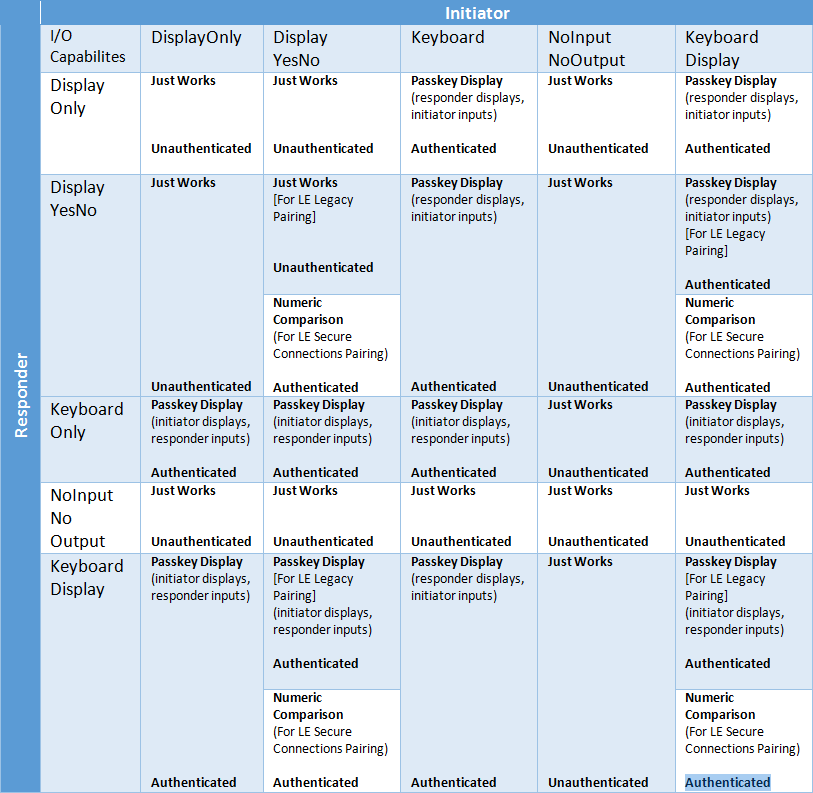
Bluetooth Pairing Part 4:Bluetooth Low EnergySecure Connections -Numeric Comparison | Bluetooth® Technology Website