
Data Security System, Information Or Network Protection. Cyber Security And Data Protection. Shield Icon, Future Technology For Verification. Abstract Circuit Board. Royalty Free Cliparts, Vectors, And Stock Illustration. Image 128279197.
What's the Difference Between Information Security and Cyber Security? | Cyber Security Career Advice


![Data Privacy vs. Data Security [definitions and comparisons] – Data Privacy Manager Data Privacy vs. Data Security [definitions and comparisons] – Data Privacy Manager](https://dataprivacymanager.net/wp-content/uploads/2019/10/Three-pillars-of-information-security-and-cybersecurity.png)

![Data Privacy vs. Data Security [definitions and comparisons] – Data Privacy Manager Data Privacy vs. Data Security [definitions and comparisons] – Data Privacy Manager](https://dataprivacymanager.net/wp-content/uploads/2020/08/visual-representation-of-data-privacy-and-data-security-areas.png)



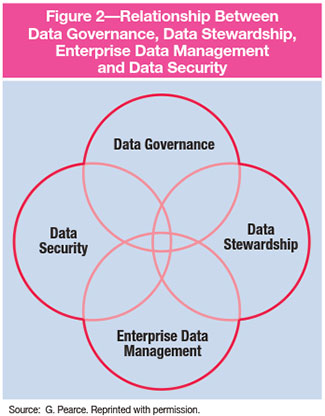


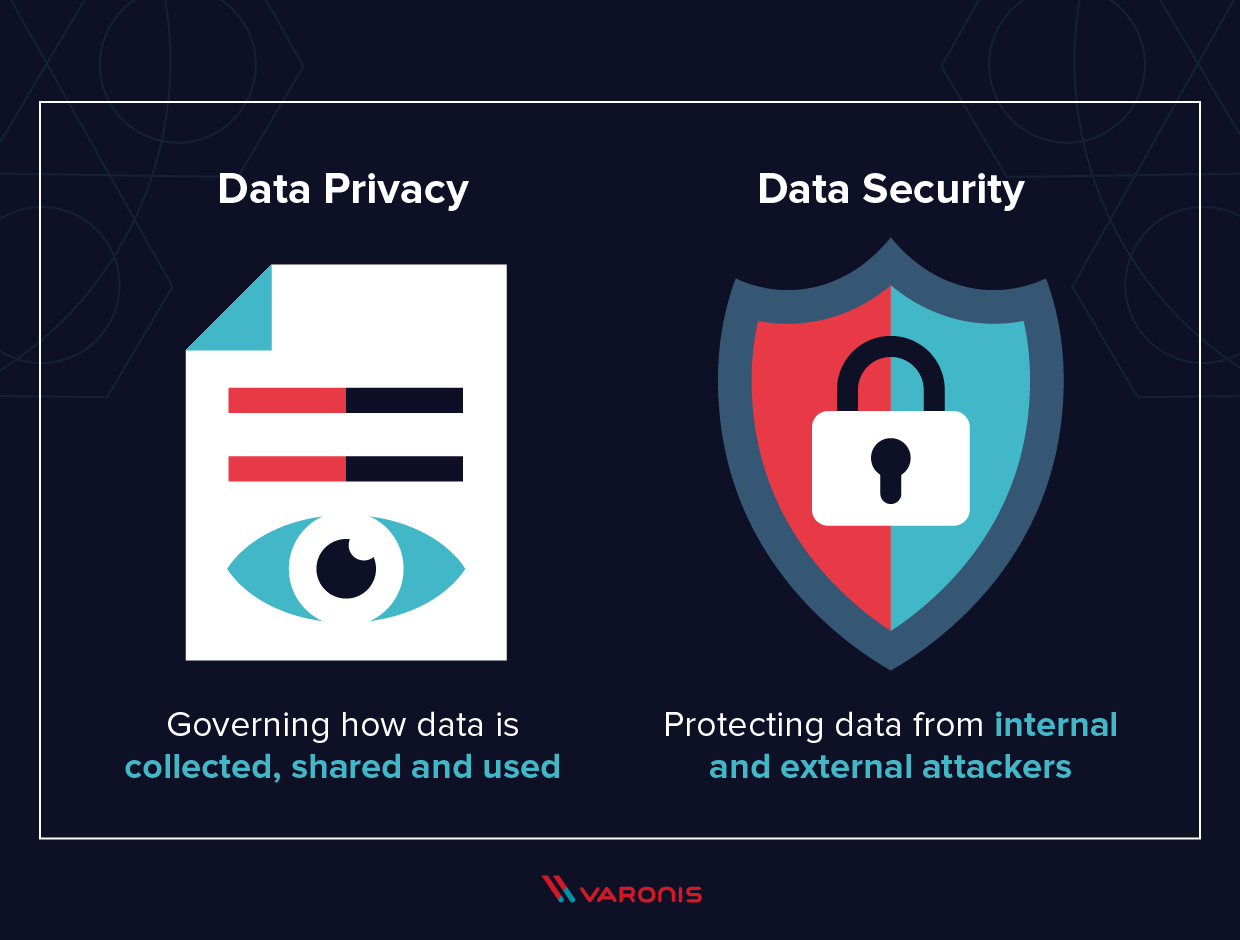




![Data Security is Not Data Privacy, Here's Why It Matters [updated for 2020] Data Security is Not Data Privacy, Here's Why It Matters [updated for 2020]](https://www.managedsolution.com/wp-content/uploads/2018/09/Data-Security-vs.-Data-Privacy-Why-it-Matters.jpg)



