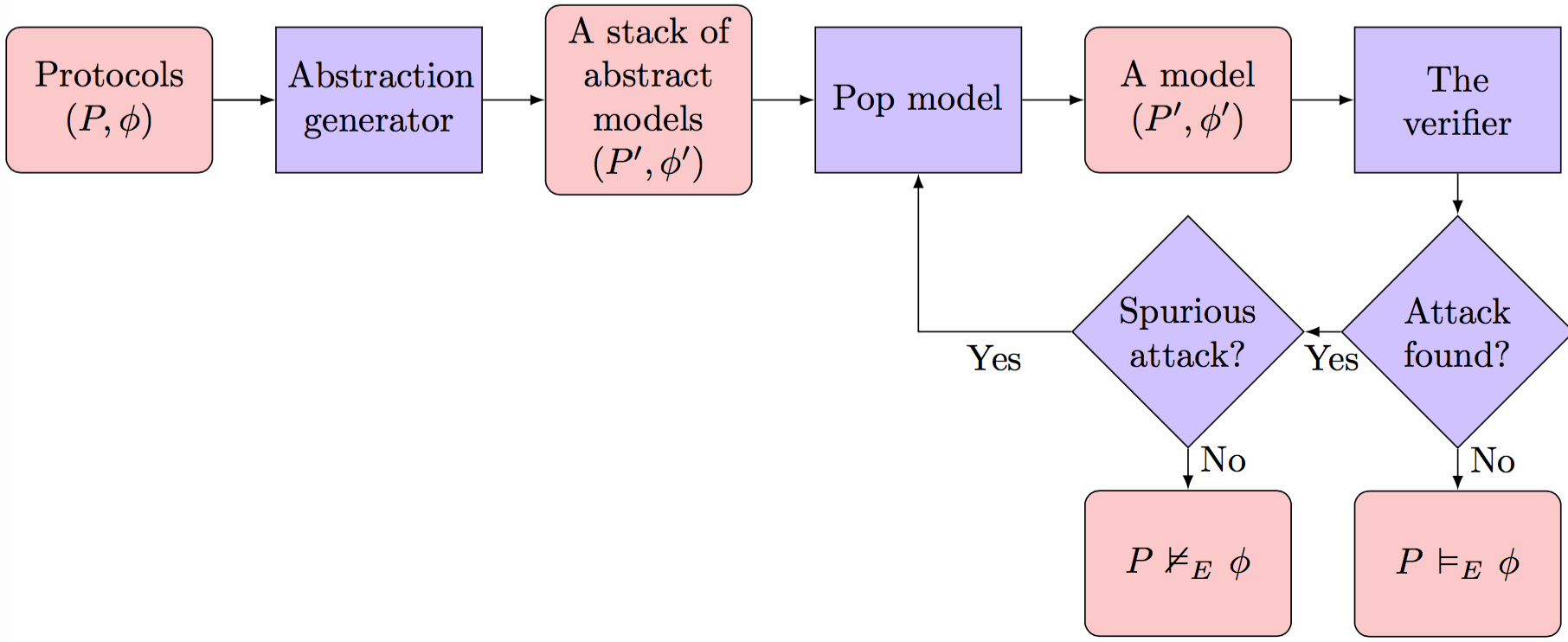
![PDF] The Scyther Tool: Verification, Falsification, and Analysis of Security Protocols | Semantic Scholar PDF] The Scyther Tool: Verification, Falsification, and Analysis of Security Protocols | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/3e8a202085b8b28e914db02ccc22201dc77dc968/2-Figure1-1.png)
PDF] The Scyther Tool: Verification, Falsification, and Analysis of Security Protocols | Semantic Scholar

A secure end‐to‐end SMS‐based mobile banking protocol - Bojjagani - 2017 - International Journal of Communication Systems - Wiley Online Library
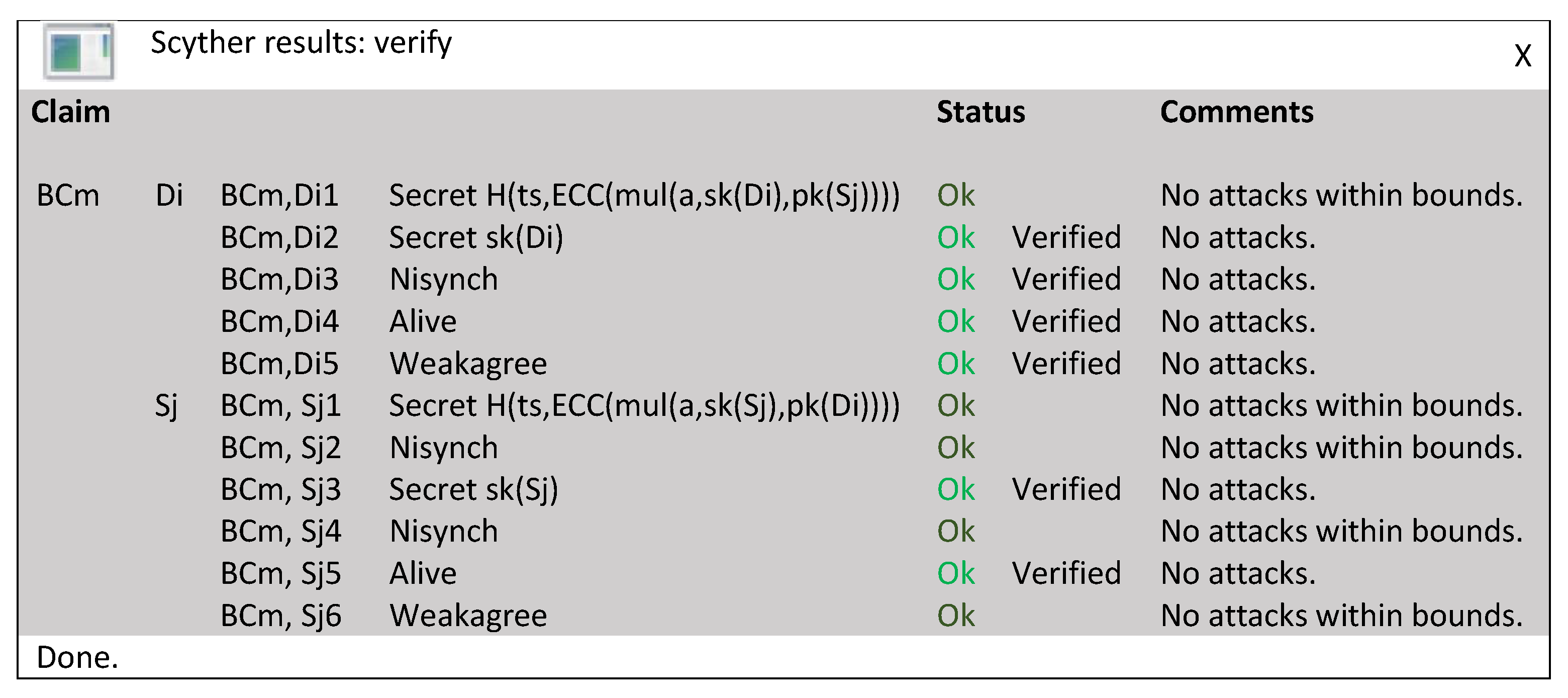
Mathematics | Free Full-Text | BCmECC: A Lightweight Blockchain-Based Authentication and Key Agreement Protocol for Internet of Things | HTML
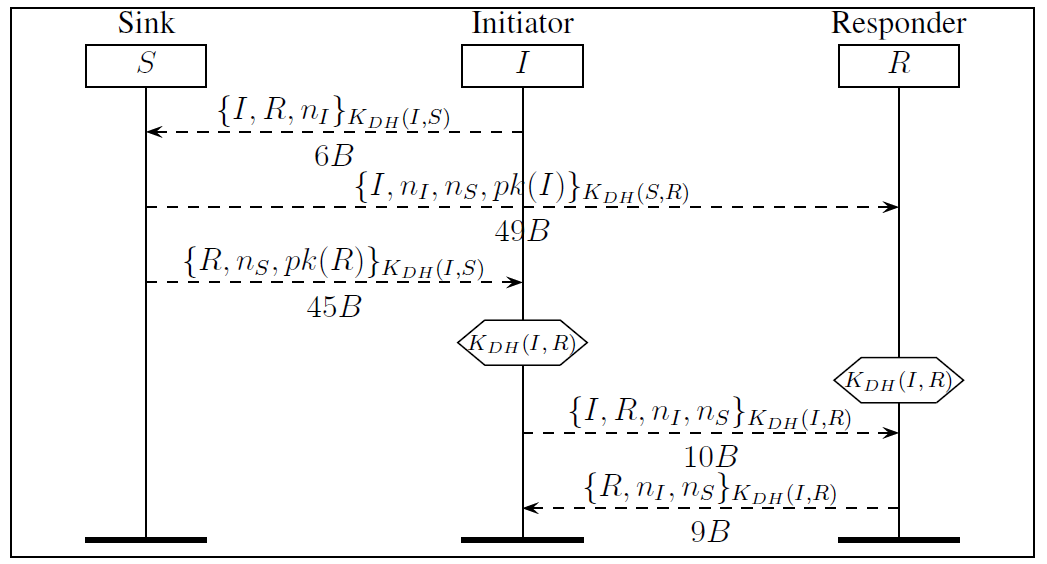
JSAN | Free Full-Text | Evaluation of Secure Multi-Hop Node Authentication and Key Establishment Mechanisms for Wireless Sensor Networks | HTML

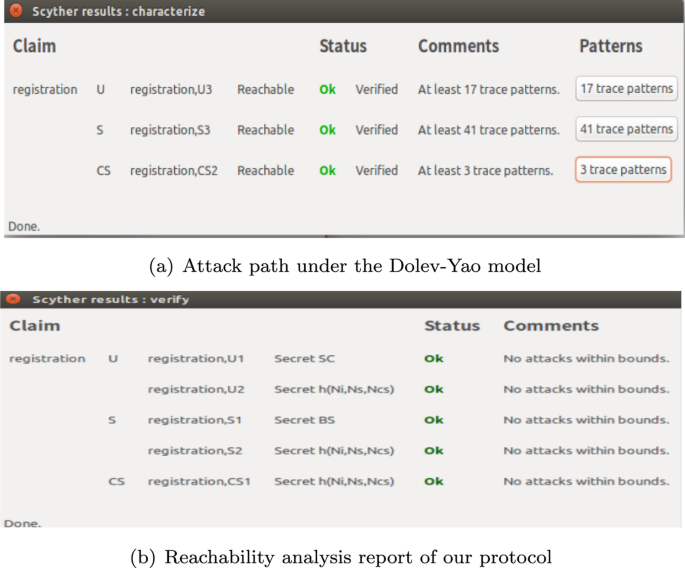
An enhanced anonymity resilience security protocol for vehicular ad-hoc network with Scyther simulation - ScienceDirect

An enhanced anonymity resilience security protocol for vehicular ad-hoc network with Scyther simulation - ScienceDirect

An enhanced anonymity resilience security protocol for vehicular ad-hoc network with Scyther simulation - ScienceDirect
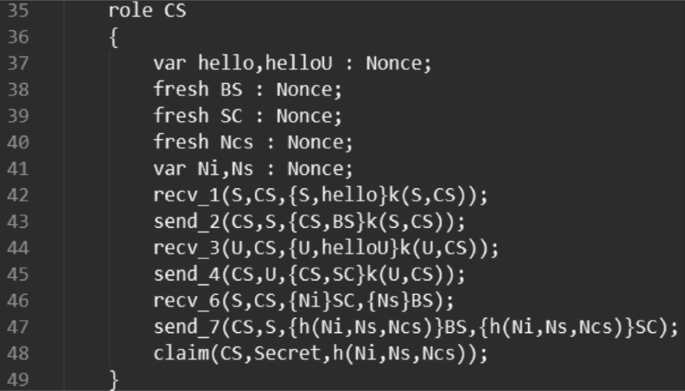
An efficient authentication and key agreement protocol for IoT-enabled devices in distributed cloud computing architecture | EURASIP Journal on Wireless Communications and Networking | Full Text

Analysis and improvement of the Internet‐Draft IKEv3 protocol - Cheng - 2017 - International Journal of Communication Systems - Wiley Online Library
GitHub - dvisionlab/Scyther: Curvilinear multiplanar reformat for Dicom Images, powered by VTK with python binding.
An efficient authentication and key agreement protocol for IoT-enabled devices in distributed cloud computing architecture | EURASIP Journal on Wireless Communications and Networking | Full Text












![PDF] Provably Repairing the ISO/IEC 9798 Standard for Entity Authentication | Semantic Scholar PDF] Provably Repairing the ISO/IEC 9798 Standard for Entity Authentication | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/a7a1181552352155e545b1328b10bd42652686b3/16-Figure9-1.png)