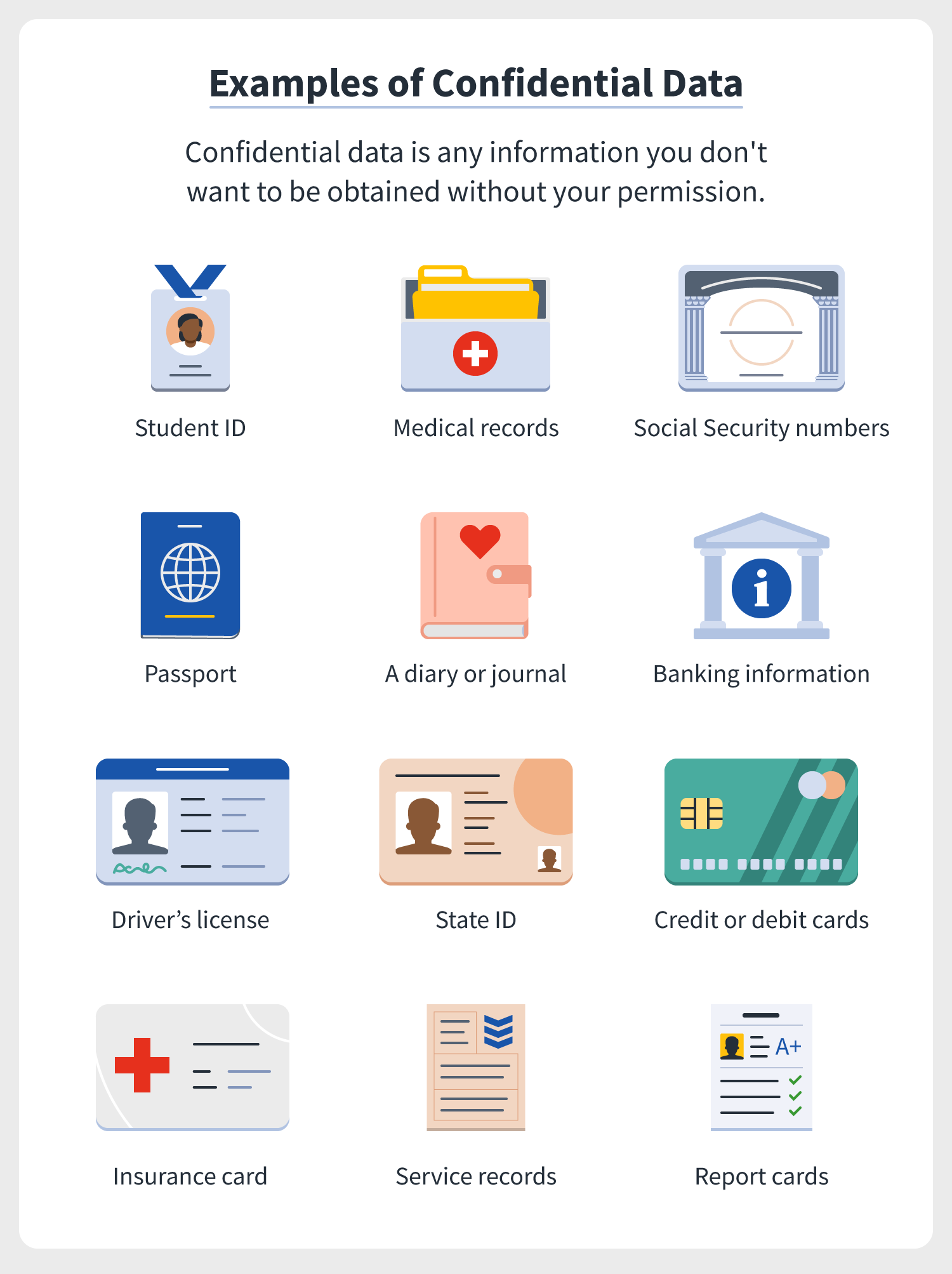
Survey: Majority of Americans put their confidential data on a piece of paper, not the cloud | Norton
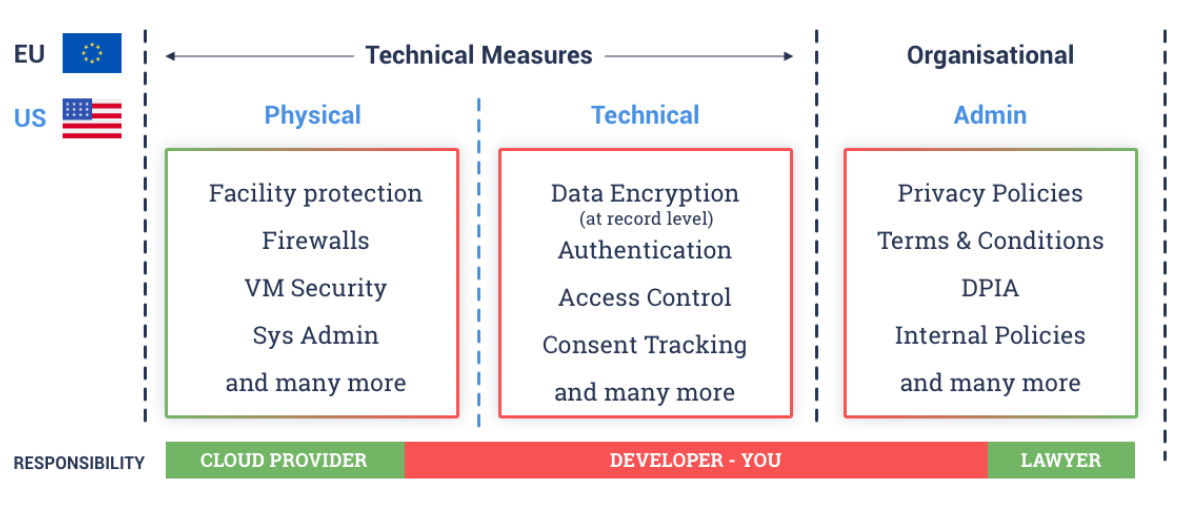
![PDF] Concepts and Tools for Protecting Sensitive Data in the IT Industry: A Review of Trends, Challenges and Mechanisms for Data-Protection | Semantic Scholar PDF] Concepts and Tools for Protecting Sensitive Data in the IT Industry: A Review of Trends, Challenges and Mechanisms for Data-Protection | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/be7b7e49864f9626be7dfbfe4c3b10bfb56d0311/7-Figure2-1.png)
PDF] Concepts and Tools for Protecting Sensitive Data in the IT Industry: A Review of Trends, Challenges and Mechanisms for Data-Protection | Semantic Scholar









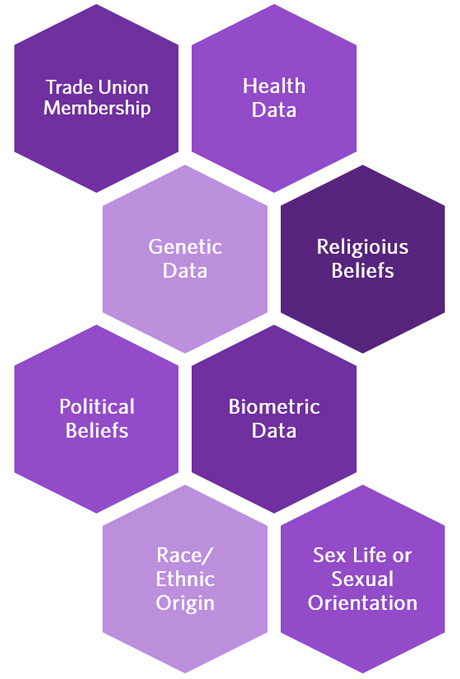

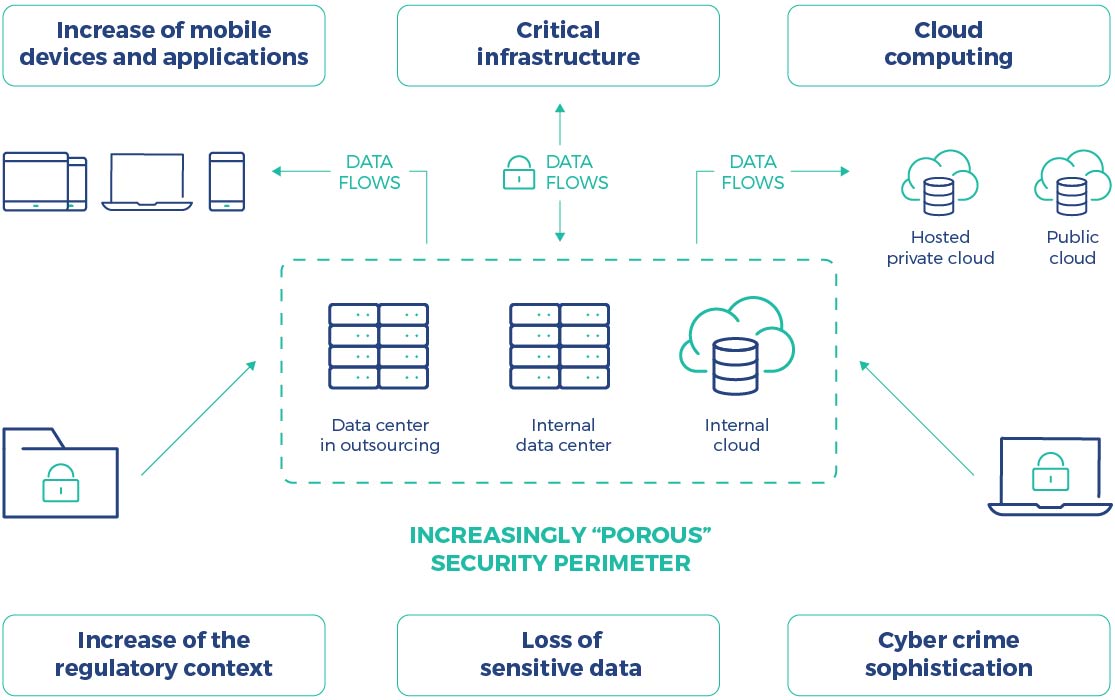

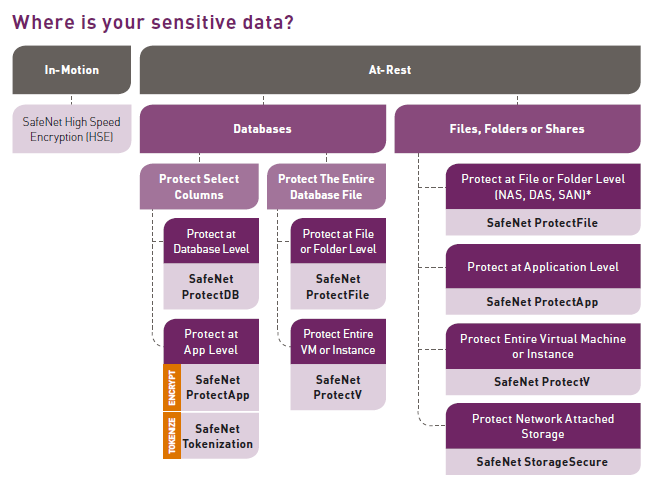

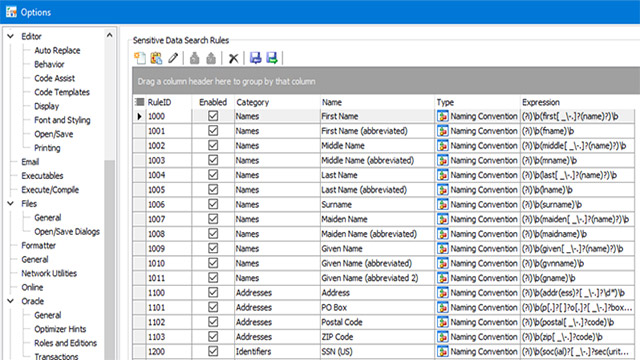


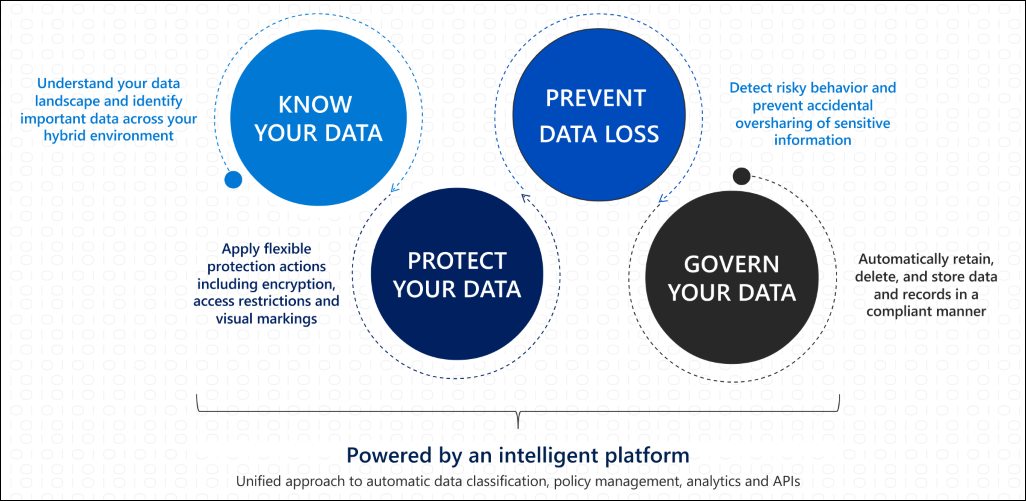

![Sensitive Data Protection Best Practices [Webinar] Sensitive Data Protection Best Practices [Webinar]](https://blog.toadworld.com/hs-fs/hubfs/GDPR_compliance_sensitive_data.jpg?width=8000&name=GDPR_compliance_sensitive_data.jpg)